With the continuous development of mobile Internet technology and the continuous improvement of mobile terminal computing capabilities, mobile terminals have gradually supported biometric identification technologies, such as Apple's mobile phone supports fingerprint recognition technology, and Samsung mobile phones support face recognition technology. This article will initially discuss how to apply the biometrics technology supported by mobile terminals to the field of mobile payment to bring users a safer and more convenient payment experience.
A biometric identification technology
Biometric Identification Technology is a new type of identification technology that integrates biotechnology and information technology. It uses the intrinsic physiological or behavioral characteristics of the human body through computer technology, optics, acoustics, and biosensors. Digitize and then use it for personal identification.
Compared with traditional identification methods, biometric identification technology has the advantages of being stable, convenient, and not easy to be counterfeited. It has become the preferred method for safety certification. In recent years, it has been widely studied and applied internationally. Some commonly used physiological features include DNA, Fingerprint, Iris, Human Face, Retina, Palm-shaped, Vein, Ear, etc. Commonly used behavioral features Including Voice, Signature, and Gait.
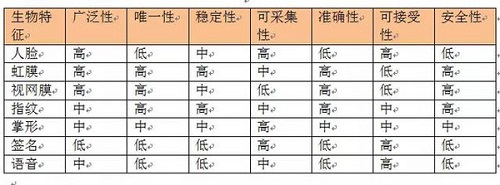
In principle, any physiological or behavioral characteristics of human beings can be used as biometrics for identification as long as they meet the conditions of universality, safety, uniqueness, stability, and collectability. The so-called universality refers to the characteristics that each individual possesses; the so-called safety refers to the fact that this feature is unique to each individual and can be used for personal identification; so-called uniqueness means that the characteristics of any two persons are not the same; The so-called stability means that the feature will not change with time and other conditions, at least for a certain period of time; the so-called collectability refers to the feature to facilitate the collection and quantitative measurement. See Table 1 for the performance comparison of several common biometric technologies.
Biometrics technology can solve two main types of problems: identity authentication and identification.
Identity authentication is to determine whether the user to be identified is his claimed identity. It is only necessary to compare the input user characteristics with the template characteristics of the identity stored in the database, which is a one-to-one comparison; the identity recognition is to use the registered user database. To determine the identity of the user to be identified, it is necessary to compare the input user characteristics with all the identity template features in the library and give a similarity to discriminate which identity in the library the user to identify is (the highest degree of similarity). A lot of comparisons.
Second, the application of biometric identification technology in the field of mobile payment
Mobile payment refers to a service mode that allows a user to use the mobile terminal to make payment for goods or services that are consumed, and is mainly divided into two types: near-field payment and remote payment. It has three characteristics: First, relying on mobile phones, tablet computers and other mobile terminals to initiate, and second, the essence is still belonging to the payment service, and the third is the diversity of payment options and innovative models are still emerging.
For mobile payment services, the authentication of the user identity that initiates the payment behavior is a crucial link, and is an important basis for the account management organization to determine whether to authorize the transaction. The information that can be used as a user authentication element can be divided into three categories: what the user knows, what the user holds, and what the user has. At present, in the mobile payment service, the commonly used identity authentication information is mainly the first two types, including online PIN, offline PIN, payment wallet PIN, identity information, card information, and a verification code. Biometrics belong to the information owned by the user. Compared with the first two types of information, the biometric features are not easy to copy, are not forgotten or lost, and are convenient to use. Along with the support of mobile terminals for biometric identification technology, they have become increasingly Many were introduced into the mobile payment field.
Third, biometric technology in mobile payment Model flowchart <br> <br> biometrics generally shown in Figure 1, comprises a user registration and user identification in two stages. In the user registration phase, the user collects the corresponding biological information through the sensor. After the preprocessing and feature extraction, the user characteristics information is entered into the registered user information database to complete the user registration; during the user identification phase, the user collects the corresponding information through the sensor and is pre-prepared After processing and feature extraction, it compares with the registered user features in the registration database and outputs the recognition result.

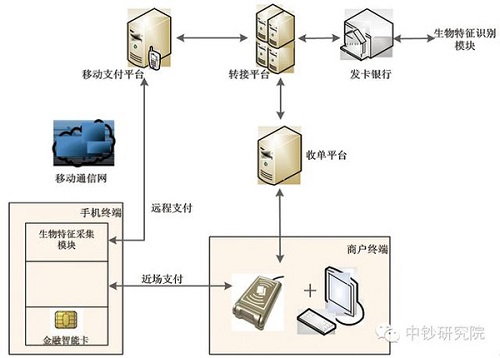
Mode 1: The mobile terminal collects user biometrics, and is responsible for the identification of users. The identity authentication technology framework is shown in Figure 2. The terminal is responsible for collecting and verifying user identity information and providing biometric CVM results during the payment process. In the process of remote payment or near field payment, the mobile payment background or terminal POS will transmit the CVM verification result through the transaction network to the issuing bank to request the transaction authorization. The issuing bank can determine whether to adopt the CVM based on its own risk control requirements. result.
The advantage of this mode is that it only depends on the mobile terminal to complete the identity authentication process and give the result. The identification process is safe and efficient, and does not need to be transmitted to the background to complete the identity authentication, which can prevent the identity authentication result from being transformed into capital loss during the transmission process.
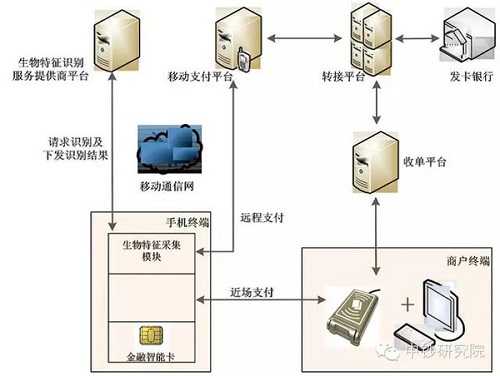
The advantage of this mode is that the mobile terminal only needs to complete the identity feature acquisition process, and the requirements for the mobile terminal are relatively low, and it is not necessary to customize and implement a specific biometric identification module. The disadvantage is that the authentication result may be tampered with in the transmission process, and the identification process takes a long time.
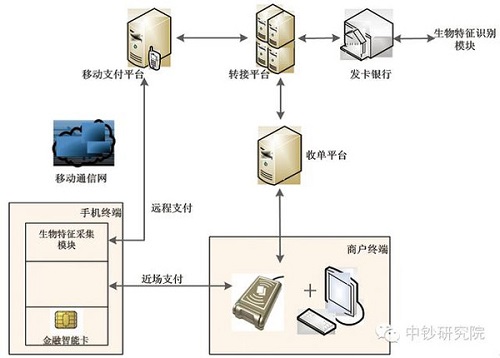
Mode 3: The mobile terminal acquires the user's biometrics, and the card is issued directly by the card issuing bank as shown in Figure 4. In the process of remote payment or near field payment, the terminal is responsible for collecting user characteristic information, and passing the collected user characteristic information to the issuing bank through the mobile payment background or the terminal POS during the transaction, and the card issuing bank identifies the user characteristic information. The CVM result is given and the CVM result is used to determine whether to authorize the transaction.
The advantage of this mode is that the mobile terminal only needs to complete the identity feature collection process, the requirements for the mobile terminal are low, and it does not need to be customized to implement a specific biometric identification module, and the CVM authentication is directly performed by the card issuing bank, and is based on the original. The online PIN verification method is consistent and easier for the issuing bank to accept. The disadvantage is that the user characteristic information with a large amount of data needs to be transmitted in the transaction message, and the transaction message in the current payment network needs to be upgraded to support.
IV Summary <br> <br> paper a preliminary analysis of the application of biometric technology to three applications in the field of mobile payments model, and a brief analysis of the advantages and disadvantages of each application of the model. With the increase of mobile terminal computing capabilities and the development of mobile Internet technologies, mobile payments will increasingly integrate with biometric technologies to provide users with safe and convenient payment products.
A biometric identification technology
Biometric Identification Technology is a new type of identification technology that integrates biotechnology and information technology. It uses the intrinsic physiological or behavioral characteristics of the human body through computer technology, optics, acoustics, and biosensors. Digitize and then use it for personal identification.
Compared with traditional identification methods, biometric identification technology has the advantages of being stable, convenient, and not easy to be counterfeited. It has become the preferred method for safety certification. In recent years, it has been widely studied and applied internationally. Some commonly used physiological features include DNA, Fingerprint, Iris, Human Face, Retina, Palm-shaped, Vein, Ear, etc. Commonly used behavioral features Including Voice, Signature, and Gait.
In principle, any physiological or behavioral characteristics of human beings can be used as biometrics for identification as long as they meet the conditions of universality, safety, uniqueness, stability, and collectability. The so-called universality refers to the characteristics that each individual possesses; the so-called safety refers to the fact that this feature is unique to each individual and can be used for personal identification; so-called uniqueness means that the characteristics of any two persons are not the same; The so-called stability means that the feature will not change with time and other conditions, at least for a certain period of time; the so-called collectability refers to the feature to facilitate the collection and quantitative measurement. See Table 1 for the performance comparison of several common biometric technologies.

Table 1 Performance comparison of several biometric identification techniques Stability Accuracy Accuracy Acceptability
Biometrics technology can solve two main types of problems: identity authentication and identification.
Identity authentication is to determine whether the user to be identified is his claimed identity. It is only necessary to compare the input user characteristics with the template characteristics of the identity stored in the database, which is a one-to-one comparison; the identity recognition is to use the registered user database. To determine the identity of the user to be identified, it is necessary to compare the input user characteristics with all the identity template features in the library and give a similarity to discriminate which identity in the library the user to identify is (the highest degree of similarity). A lot of comparisons.
Second, the application of biometric identification technology in the field of mobile payment
Mobile payment refers to a service mode that allows a user to use the mobile terminal to make payment for goods or services that are consumed, and is mainly divided into two types: near-field payment and remote payment. It has three characteristics: First, relying on mobile phones, tablet computers and other mobile terminals to initiate, and second, the essence is still belonging to the payment service, and the third is the diversity of payment options and innovative models are still emerging.
For mobile payment services, the authentication of the user identity that initiates the payment behavior is a crucial link, and is an important basis for the account management organization to determine whether to authorize the transaction. The information that can be used as a user authentication element can be divided into three categories: what the user knows, what the user holds, and what the user has. At present, in the mobile payment service, the commonly used identity authentication information is mainly the first two types, including online PIN, offline PIN, payment wallet PIN, identity information, card information, and a verification code. Biometrics belong to the information owned by the user. Compared with the first two types of information, the biometric features are not easy to copy, are not forgotten or lost, and are convenient to use. Along with the support of mobile terminals for biometric identification technology, they have become increasingly Many were introduced into the mobile payment field.
Third, biometric technology in mobile payment Model flowchart <br> <br> biometrics generally shown in Figure 1, comprises a user registration and user identification in two stages. In the user registration phase, the user collects the corresponding biological information through the sensor. After the preprocessing and feature extraction, the user characteristics information is entered into the registered user information database to complete the user registration; during the user identification phase, the user collects the corresponding information through the sensor and is pre-prepared After processing and feature extraction, it compares with the registered user features in the registration database and outputs the recognition result.

Figure 1 Flow chart of biometric identification
When applied to the field of mobile payment, biometrics technology is mainly to solve the problem of identity authentication. The specific application scenario can combine the user identity authentication technology based on the biometric identification technology with the user to open a wallet, set a default payment account, activate a payment application, and act as a Cardholder Verification Method (CVM) during the payment process. . The following mainly describes the use of CVM in the payment process. According to different entities that perform feature recognition steps, they can be classified into three categories: mobile terminal local authentication, biometric service provider platform certification, and card issuer certification. Mode 1: The mobile terminal collects user biometrics, and is responsible for the identification of users. The identity authentication technology framework is shown in Figure 2. The terminal is responsible for collecting and verifying user identity information and providing biometric CVM results during the payment process. In the process of remote payment or near field payment, the mobile payment background or terminal POS will transmit the CVM verification result through the transaction network to the issuing bank to request the transaction authorization. The issuing bank can determine whether to adopt the CVM based on its own risk control requirements. result.
The advantage of this mode is that it only depends on the mobile terminal to complete the identity authentication process and give the result. The identification process is safe and efficient, and does not need to be transmitted to the background to complete the identity authentication, which can prevent the identity authentication result from being transformed into capital loss during the transmission process.

Fig. 2 Model-technical framework
Mode 2: The mobile terminal collects user biometrics. The biometric service provider platform is responsible for identifying the identity and returns the results to the mobile terminal. The technical framework diagram is shown in Figure 3. The terminal is responsible for collecting user characteristic information, and then sends it to the biometric service provider platform for identification. The service provider platform returns the recognition result to the mobile terminal. In the process of remote payment or near field payment, the mobile payment background or terminal POS will pass the recognition result to the issuing bank through the transaction network to request the transaction authorization. The issuing bank can determine whether to adopt the CVM result based on its own risk control requirements. The advantage of this mode is that the mobile terminal only needs to complete the identity feature acquisition process, and the requirements for the mobile terminal are relatively low, and it is not necessary to customize and implement a specific biometric identification module. The disadvantage is that the authentication result may be tampered with in the transmission process, and the identification process takes a long time.

Figure 3 Mode 2 Technology Framework
Mode 3: The mobile terminal acquires the user's biometrics, and the card is issued directly by the card issuing bank as shown in Figure 4. In the process of remote payment or near field payment, the terminal is responsible for collecting user characteristic information, and passing the collected user characteristic information to the issuing bank through the mobile payment background or the terminal POS during the transaction, and the card issuing bank identifies the user characteristic information. The CVM result is given and the CVM result is used to determine whether to authorize the transaction.

Figure 4 Mode 3 Technical Framework
The advantage of this mode is that the mobile terminal only needs to complete the identity feature collection process, the requirements for the mobile terminal are low, and it does not need to be customized to implement a specific biometric identification module, and the CVM authentication is directly performed by the card issuing bank, and is based on the original. The online PIN verification method is consistent and easier for the issuing bank to accept. The disadvantage is that the user characteristic information with a large amount of data needs to be transmitted in the transaction message, and the transaction message in the current payment network needs to be upgraded to support.
IV Summary <br> <br> paper a preliminary analysis of the application of biometric technology to three applications in the field of mobile payments model, and a brief analysis of the advantages and disadvantages of each application of the model. With the increase of mobile terminal computing capabilities and the development of mobile Internet technologies, mobile payments will increasingly integrate with biometric technologies to provide users with safe and convenient payment products.
High Power Laser Cutting Machine
Super-power, for thick and thin plates
Equipped with high/super power laser device, efficient thick plate cutting is no longer a dream, thin plate cutting is more speedy; BODOR database of cutting process will provide you with data support of performance and energy saving to save your cutting cost. Tailor-made high power laser machine for customers, its maximum cutting range includes 50mm aluminium plate, 30mm stainless steel and 25mm carbon steel plate.
High Power Laser Cutting Machine,Fiber Laser Cutter,High Power Laser Cutting Machine
Jinan Bodor CNC Machine Co., Ltd. , https://www.bodorcnc.com